Get Started with Teleport
Teleport Enterprise helps organizations provide secure access to their infrastructure with minimal configuration and cluster management.
With Teleport Enterprise (Cloud), the Teleport Auth Service and Teleport Proxy Service are managed for you as cloud-based services. These services provide you with immediate access to a scalable and fault-tolerant certificate authority and reverse proxy that you don't need to manage or maintain. You can focus on enrolling the resources you want to protect and configuring secure role-based access for private and public networks across the globe.
After you start a free trial of Teleport Enterprise (Cloud), you can set up role-based access control (RBAC), enable single sign-on, and prevent unauthorized use of organization resources.
This guide explains how to register a local server with a Teleport Enterprise (Cloud) account. After you register the server, you can access it through the Teleport Web UI in a browser or using the terminal. You can also record your sessions, so you can review them later.
Prerequisites
-
A Teleport Enterprise (Cloud) account. You can sign up for a free trial at the following page:
https://goteleport.com/signup/
After you sign up, you receive an email invitation to activate your account. Use this account to authenticate your identity when you access the Teleport Enterprise (Cloud) cluster.
-
Docker installed on your workstation.
This guide illustrates how to register a server with Teleport Enterprise Cloud using a Docker container and the Teleport SSH Service. Docker is only required for the local demo environment used in this guide. You can find installation instructions for Docker on Docker's website. If you want to register servers in Teleport without using Docker, see the getting started guide for server access.
-
The
tshclient tool.The
tshclient tool is only required to access the server from a terminal. For installation instructions, see Installation Guide. If you don't install thetshclient tool, you can access the server in Teleport Enterprise (Cloud) using the Web UI through your browser.
Step 1/5. Spin up a server
To spin up a new server using Docker:
-
Open a terminal shell on your workstation.
-
Start a Docker container on your workstation to prepare a server that you want enroll as a resource in your Teleport Enterprise (Cloud) cluster:
$ docker run --interactive --tty ubuntu:22.04 /bin/bashThis command starts a new shell session in the
ubuntu:22.04container. -
Run the following command to install
curlandtelnetfrom the package management repository:$ apt update && apt install -y curl telnetThe script that installs Teleport in this guide requires both
curlandtelnetto be installed.Keep the new shell open in your terminal.
Step 2/5. Install the Teleport SSH Service
To install the Teleport SSH Service on your server:
-
Open a browser and go to the address for your Teleport cluster. For example, if your Teleport account is
example, openhttps://example.teleport.sh. -
Sign in with the account credentials you used to activate your Teleport account.
The first time you sign in, you are prompted to add your first resource:
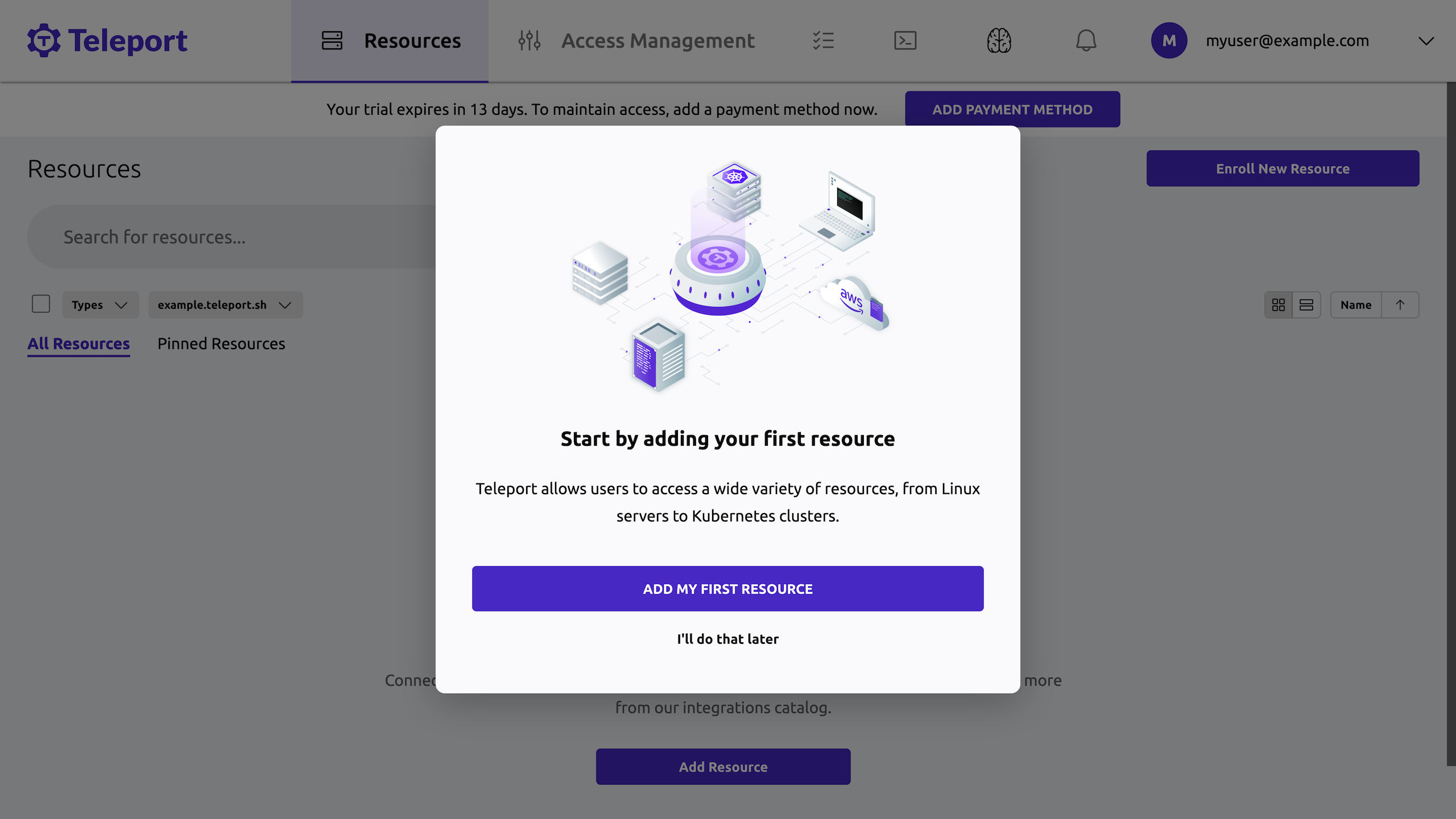
-
Click Add my first resource, and you will see the option to enroll resources in your Teleport cluster.
-
Type server in the search box to filter the list of resources:
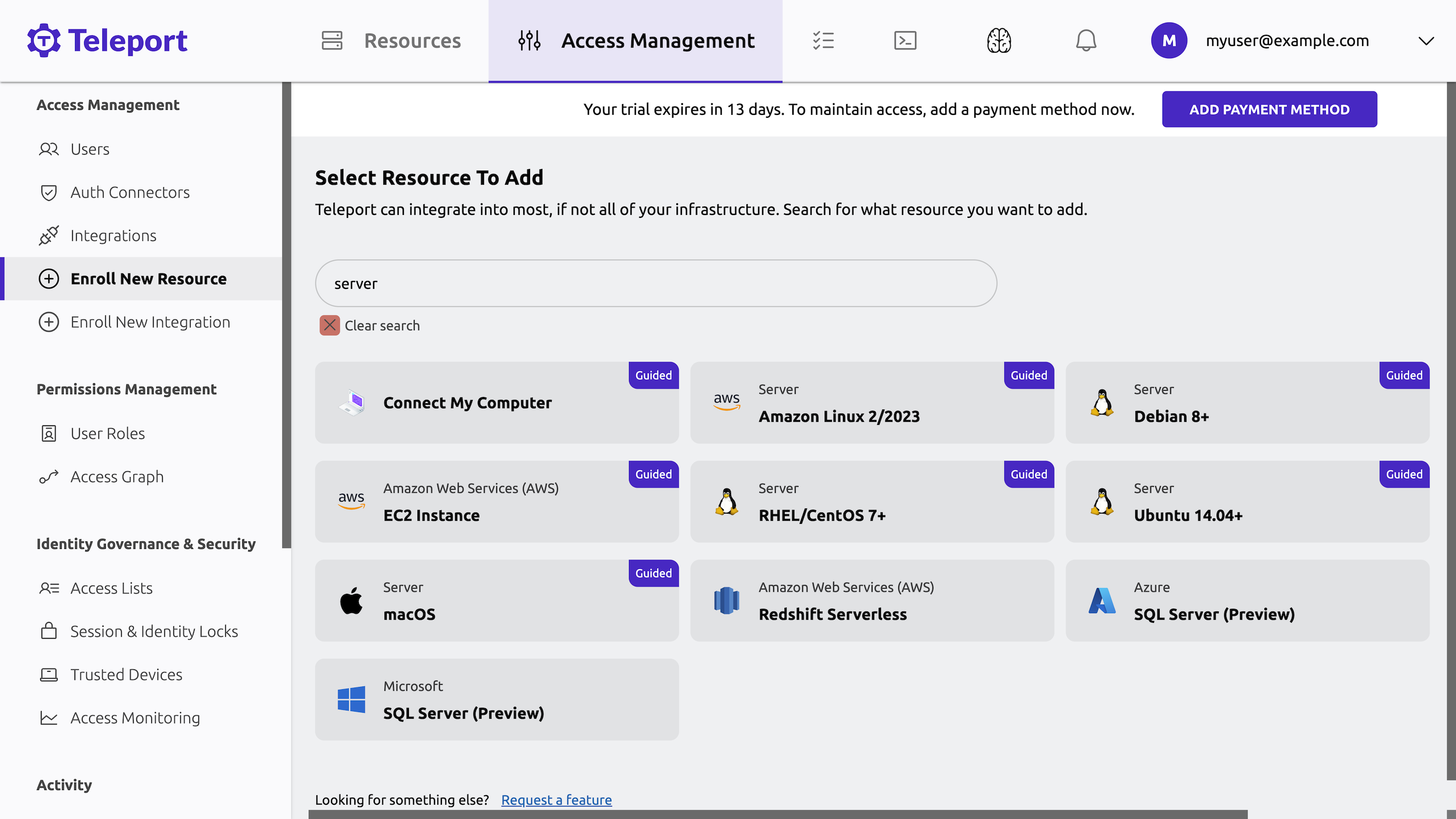
-
Click Ubuntu 14.04+ to register the server in the Docker container.
After you select Ubuntu 14.04+ as the resource type, the Web UI prompts you for your multi-factor authentication device, then displays a script to install and configure the Teleport SSH Service. For example:
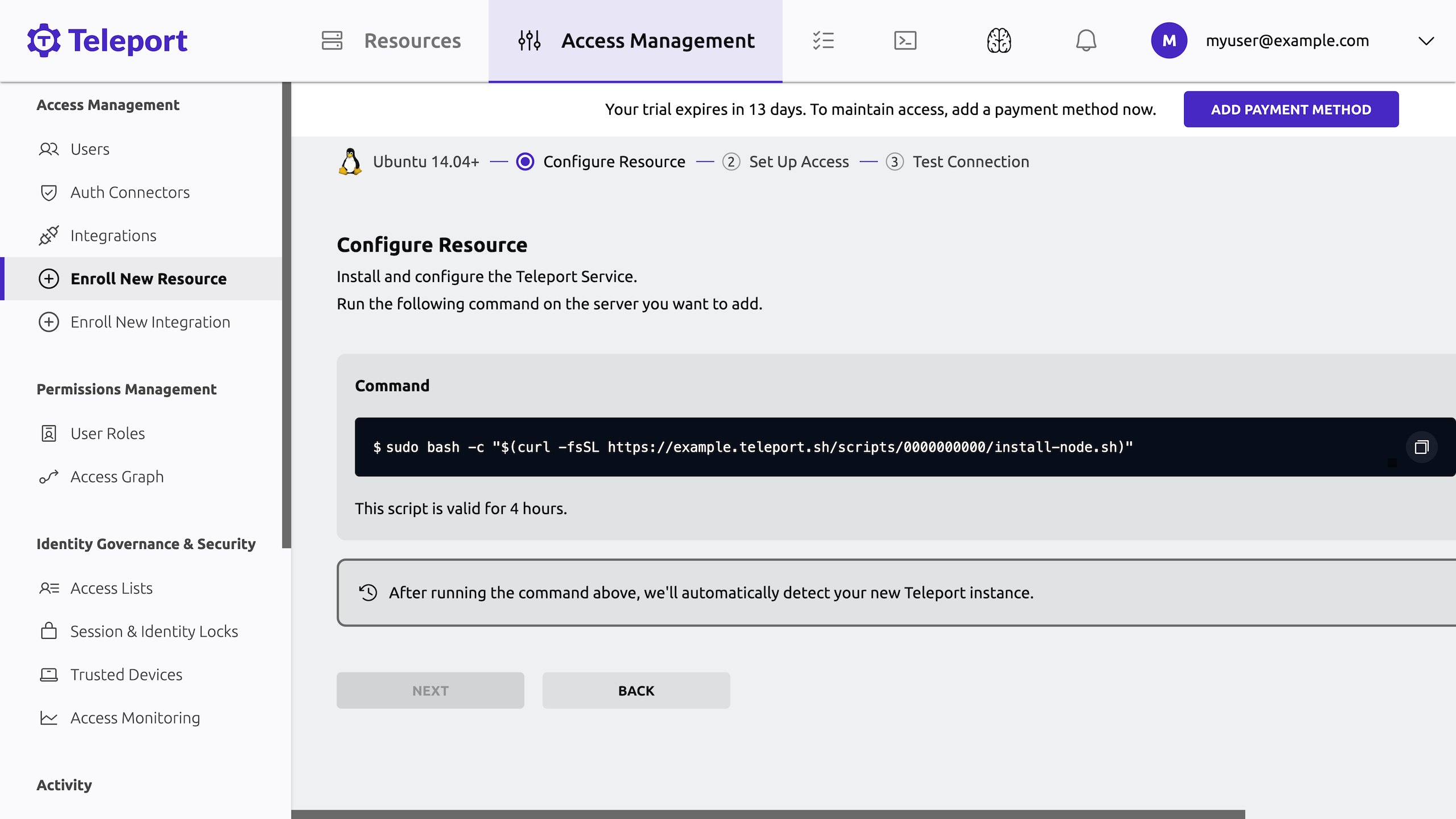
-
The Teleport installation script uses
sudo, which is not installed on your Docker container. Before copying the command to run the installation script, you need to aliassudoin the container terminal shell session.In the terminal with the container shell session, alias
sudoby running the following command:$ alias sudo="" -
Copy the command to run the installation script from the Teleport Web UI and paste it into the container shell session.
Leave the script running in the shell. After Teleport is installed on the server, you'll see a message in the Web UI that your new Teleport instance was successfully detected:
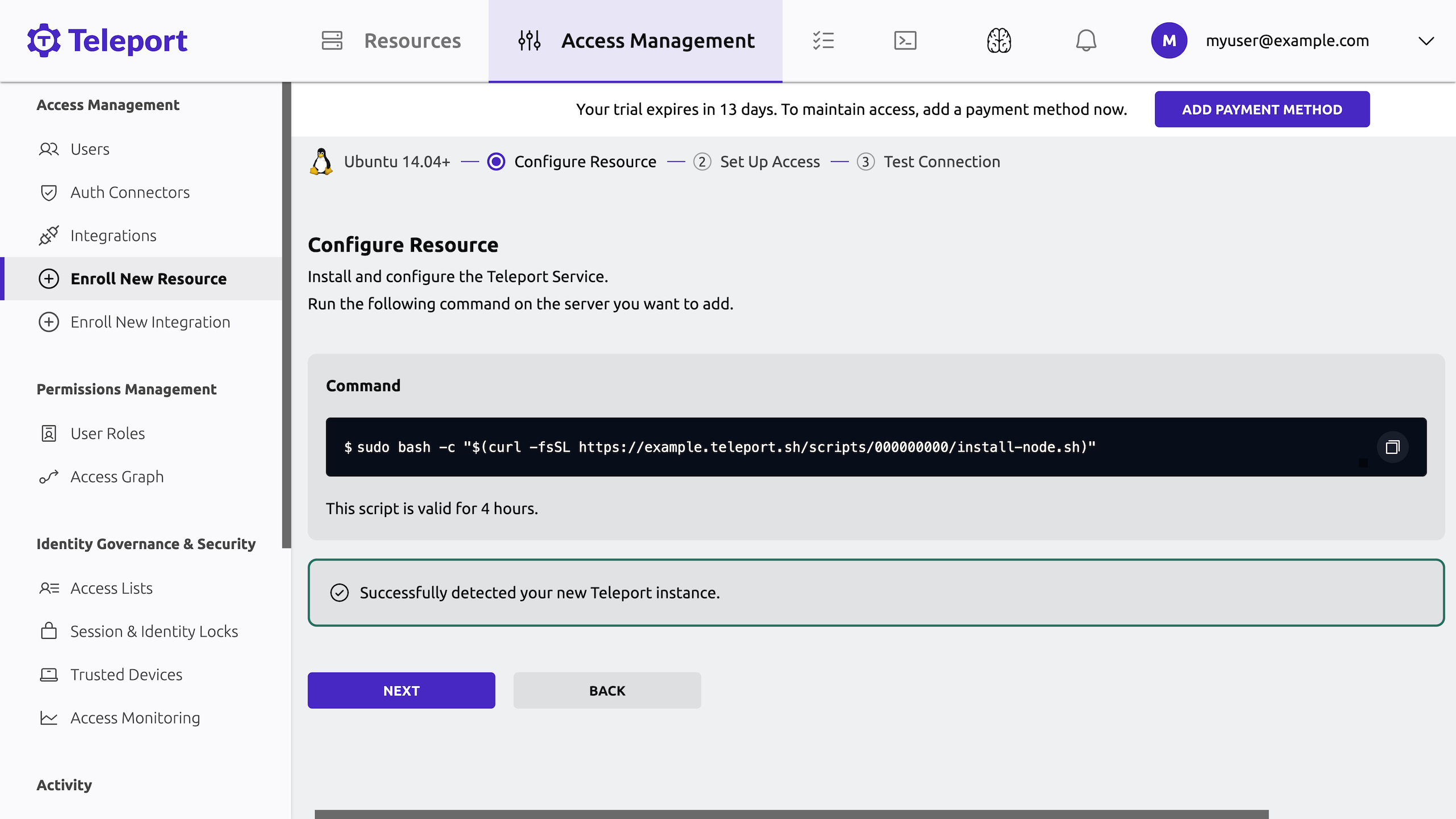
To continue, click Next.
-
Confirm that you want to authenticate as the
rootuser and click Next: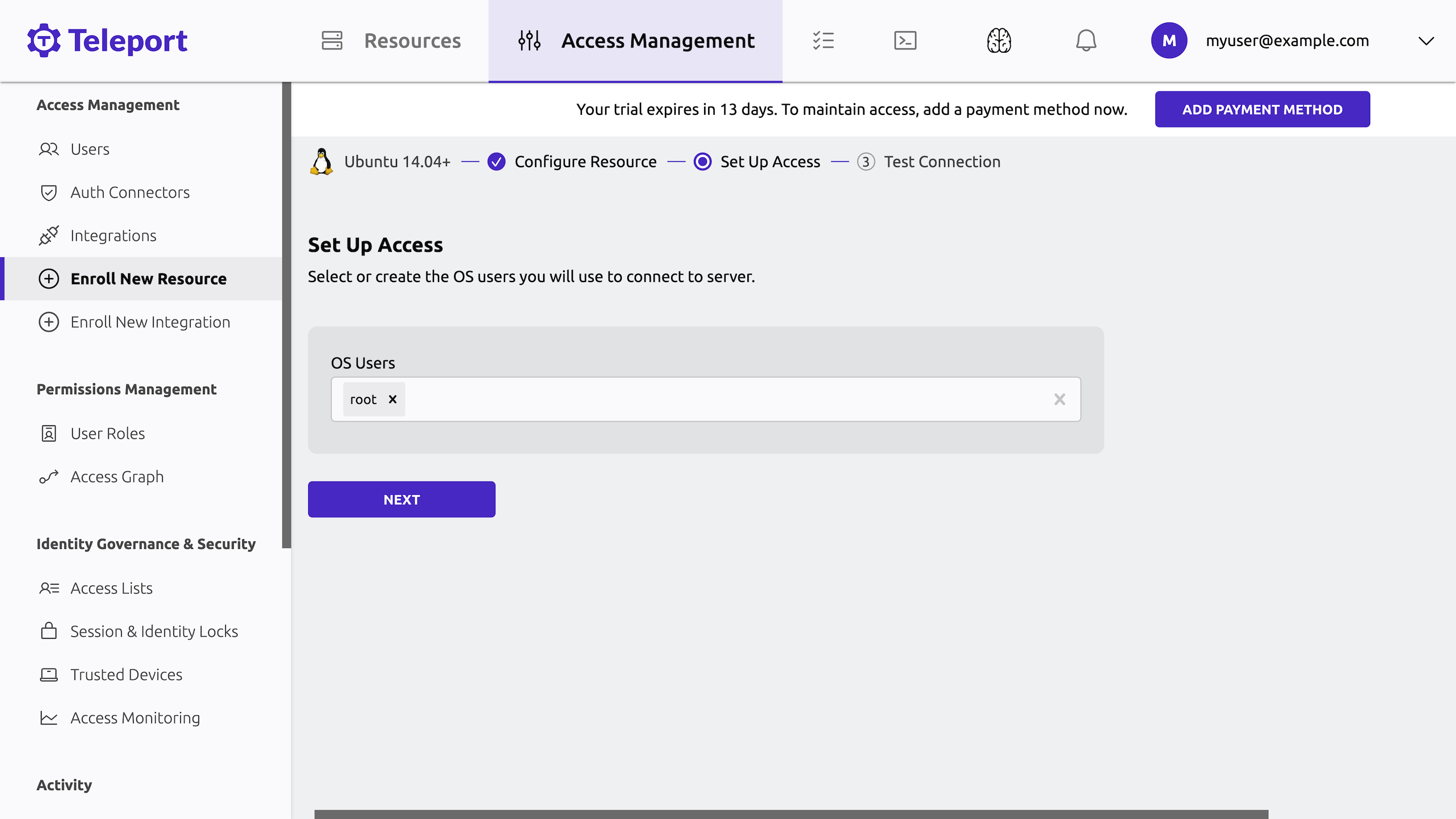
-
Respond to the MFA prompt again, then click Test Connection to verify access to the server.
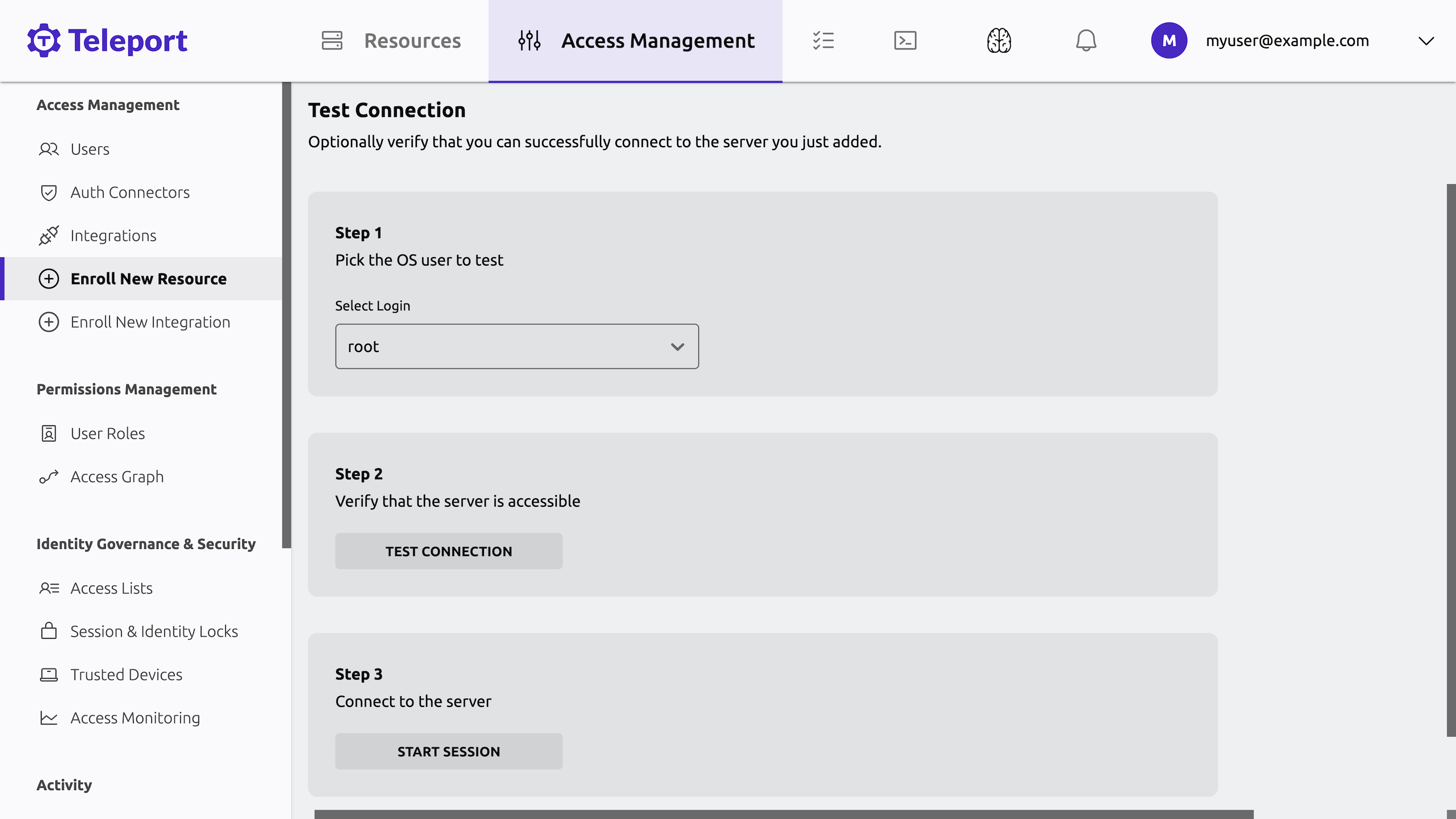
Step 3/5. Start a session
To start a session on the server you just added to Teleport:
-
Click Start Session to start an interactive session.
You should see a terminal prompt in a new browser window. Your Teleport account routes your SSH connection through the Teleport Proxy Service, which connects to your container through a reverse tunnel. Reverse tunnels allow Teleport to manage access to resources like Kubernetes clusters and remote desktops, even if these resources are running on private networks.
If you get an error connecting to your container, interrupt the
teleportprocess in the container shell with Ctrl-C, then runteleport startto restart the process. -
Execute some commands in your terminal.
-
Enter the
exitcommand to end the remote interactive session. Close the browser tab. -
In the last step of Enroll New Resource, click Finish.
-
Click Browse existing resources to see your new server listed in the Teleport Web UI.
Step 4/5. Play back your session
As Teleport proxies SSH connections to registered servers, it records the commands that users execute during their sessions so operators can play them back later to investigate issues.
To play back a session in the Teleport Web UI:
-
Click the Access Management tab at the top of the window.
-
In the sidebar, under Activity, click Session Recordings.
You will see the recording for your interactive session from the previous step listed. For example:
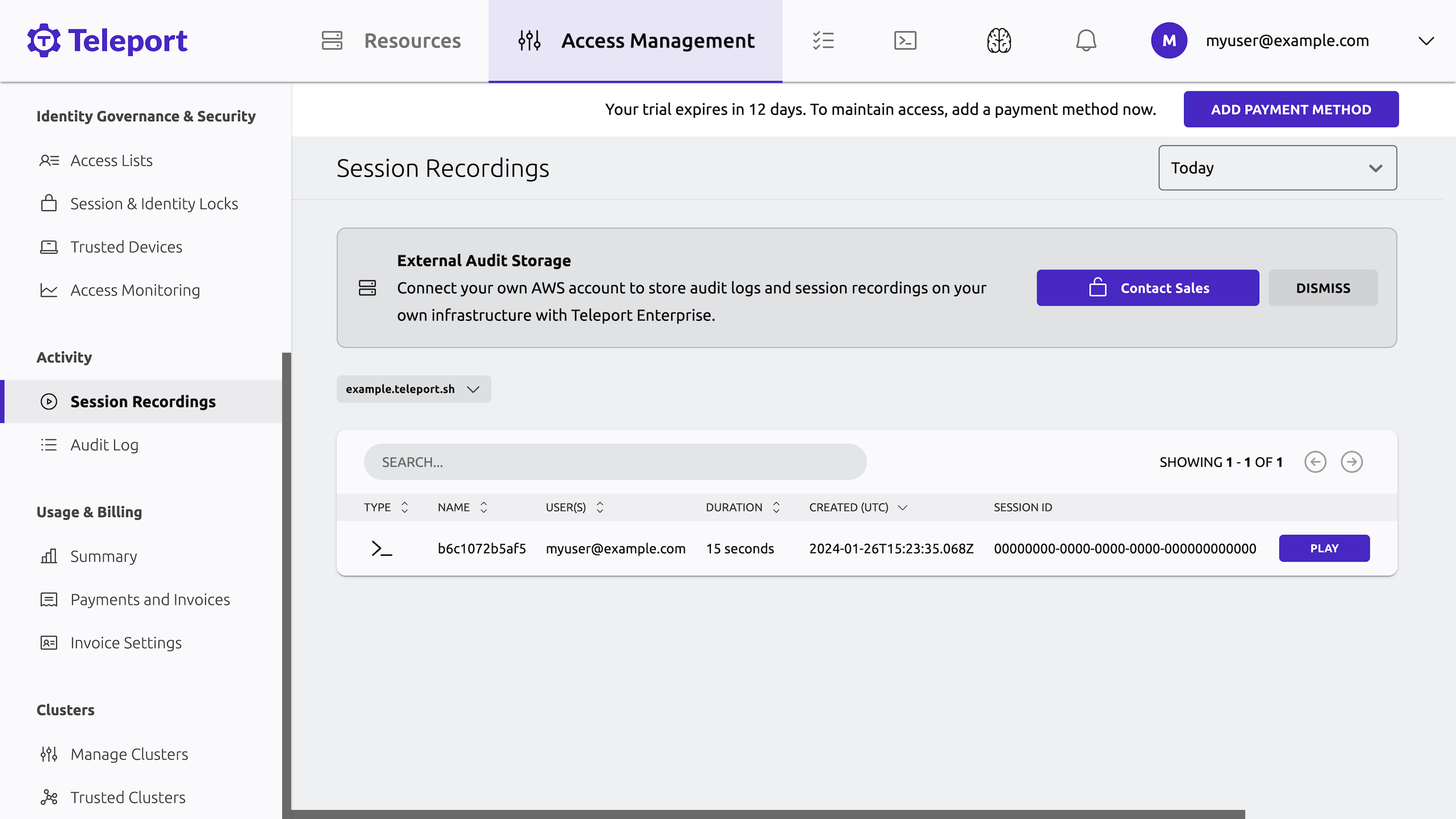
-
Click Play to see a full recording of your session.
Step 5/5. Access the server from the command line
To access the server using commands in a terminal:
-
Open a new terminal window.
-
Sign in to your Teleport cluster by running the
tsh logincommand with the URL of your cluster and the name of your Teleport user:$ tsh login --proxy=example.teleport.sh --user=usernameWhen prompted, authenticate using your password, authenticator app, or hardware key. The command displays information about your Teleport cluster and account. For example:
> Profile URL: https://example.teleport.sh:443
Logged in as: admin@teleport.example.com
Cluster: example.teleport.sh
Roles: access, auditor, editor
Logins: root
Kubernetes: enabled
Valid until: 2023-07-08 01:35:20 -0700 PDT [valid for 12h0m0s]
Extensions: login-ip, permit-agent-forwarding, permit-port-forwarding, permit-pty, private-key-policy -
List the servers your Teleport user can access.
$ tsh lsYou should see the name of the container you just registered. For example:
Node Name Address Labels
------------ --------- ----------------------------------------------------------------------------------------
b6c1072b5af5 ⟵ Tunnel hostname=b6c1072b5af5 -
Access your server as the
rootuser:$ tsh ssh root@node-name
Next steps
This guide introduced how you can use Teleport Enterprise (Cloud) to protect your infrastructure by demonstrating how to register a server with your Teleport cluster.
You can provide secure access to more of your infrastructure through Teleport by deploying one or more Teleport agents and configuring role-based access control for users.
Agents proxy traffic to all of your infrastructure resources—including servers, databases, Kubernetes clusters, cloud provider APIs, and Windows desktops. Role-based access control ensures that only authorized users are allowed access to those resources.
To learn more information about deploying agents, see Deploy Teleport Agents with Terraform.